Virus Shortcut Remover Windows 7
Download pc shortcut virus remover windows 10 for free. Security tools downloads - Shortcut Virus Remover by prokash and many more programs are available for instant and free download. Download Shortcut Virus Remover. A simple to use tool that enables you to clean the shortcut virus from your USB drives and even immunize them against future threats.
- Virus Shortcut Remover Windows 7 Windows 10
- How To Remove Shortcut Virus From Laptop
- Shortcut Virus Remover Windows 7 32 Bit
You must be logged in as an administrator to be able to do the steps in this tutorial.
You can still tell by right clicking or press and hold on the file, and click/tap on Properties to see if you have a Shortcut tab or not.
32-bit (x86) Windows2. Double click/tap on the program's shortcut to run the program.
64-bit (x64) Windows
3.To Change, Restore, or Remove the Arrow for All Shortcuts
A) Select (dot) the arrow option you want for the shortcut arrow. (See screenshot below)4. To Remove the 'Shortcut' Name from All Shortcuts
NOTE:If you selected Custom Arrow to change the shortcut arrow, then click on Select and navigate to and choose a ICO (icon) file you have downloaded to use as the shortcut arrow.
NOTE:See also: Shortcut Extension - Remove or Restore
A) Check the box to also remove the - Shortcut name extension for new shortcuts that are created.5. Click/tap on Apply.
6. Click/tap on Yes to log off to apply the changes. (See screenshot below)
NOTE:If you like, you could also just restart explorer instead to apply your changes.
7. Log back on and your done.
The Arrow (default) and Custom Arrow options will not be undone if you uninstall 'Vista Shortcut Overlay Remover'.
2. In regedit, navigate to the location below:
NOTE:If Shell Icons it is not in the left pane under Explorer, right click on Explorer, and click on New and Key. Type Shell Icons for the new keys's name, and press Enter.
3. In the right pane of
 Shell Icons, right click on an empty area, and click/tap on New and String Value, and name it 29.
Shell Icons, right click on an empty area, and click/tap on New and String Value, and name it 29.4. Double click/tap on the 29 sting value to modify it.
5. Type in the full path of your custom .ico file within quotes, OR
 copy and paste the path below for what overlay icon you would like to use, and click/tap on OK.
copy and paste the path below for what overlay icon you would like to use, and click/tap on OK.(No arrow - Transparent) %windir%System32shell32.dll,-506. Log off and on, or restart the computer to apply.
(Classic) %windir%System32shell32.dll,-30
(Default) %windir%System32shell32.dll,-16769
NOTE:This option does the same thing as OPTION TWO above, but automatically for you using a .reg file.
1. Do step 2, 3, or 4 below for what you would like to do.That's it,
2. To Restore Default Shortcut Arrow Overlay Icon
NOTE:This is the default setting.A) Click/tap on the Download button below to download the .reg file below, and go to step 5 below.3. To Use Classic Shortcut Arrow Overlay Icon
Default_Shortcut_Arrow.regA) Click/tap on the Download button below to download the .reg file below, and go to step 5 below.4. To Have No Shortcut Arrow Overlay Icon
Classic_Shortcut_Arrow.regA) Click/tap on the Download button below to download the .reg file below, and go to step 5 below.5. Log off and log on, or restart the computer to apply.
No_Shortcut_Arrow.reg
6. You can now delete the downloaded .reg file if you like.
Shawn
Do a full system scan
Let us know the results at the end.
http://www.malwarebytes.org/products
Windows Insider MVP
MVP-Windows and Devices for IT
http://www.zigzag3143.com/
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
www.malwarebytes.org
Scan Date: 18-06-2015
Scan Time: AM 11:36:54
Logfile: result.txt
Administrator: Yes
Version: 2.01.6.1022
Malware Database: v2015.06.18.01
Rootkit Database: v2015.06.15.01
License: Trial
Malware Protection: Enabled
Malicious Website Protection: Enabled
Self-protection: Disabled
OS: Windows 7
CPU: x64
File System: NTFS
User: pandu
Scan Type: Threat Scan
Result: Completed
Objects Scanned: 337882
Time Elapsed: 20 min, 6 sec
Memory: Enabled
Startup: Enabled
Filesystem: Enabled
Archives: Enabled
Rootkits: Disabled
Heuristics: Enabled
PUP: Enabled
PUM: Enabled
Processes: 0
(No malicious items detected)
Modules: 0
(No malicious items detected)
Registry Keys: 2
PUP.Optional.WinYahoo.A, HKLMSOFTWAREMICROSOFTINTERNET EXPLORERSEARCHSCOPES{0633EE93-D776-472F-A0FF-E1416B8B2E3A}, , [85a4ead20684f4422e993a52bb4ae818],
PUP.Optional.WinYahoo.A, HKUS-1-5-21-2887370976-2933954842-197170916-1001SOFTWAREMICROSOFTINTERNET EXPLORERSEARCHSCOPES{0633EE93-D776-472F-A0FF-E1416B8B2E3A}, , [a88118a494f666d09234f19b9b6ab34d],
Registry Values: 4
PUP.Optional.WinYahoo.A, HKLMSOFTWAREMICROSOFTINTERNET EXPLORERSEARCHSCOPES{0633EE93-D776-472f-A0FF-E1416B8B2E3A} URL, http://in.yhs4.search.yahoo.com/yhs/search?hspart=iry&hsimp=yhs-fullyhosted_003&type=wncy_ir_15_25¶m1=1¶m2=fD4%26bDIE%26ccDin%26paDWincy%26cdD2XzuyEtN2Y1L1QzutDtDtAtDyCyByD0Ezz0DtDyByC0Bzy0AtN0D0Tzu0StCtByCtBtN1L2XzutAtFtCtDtFtCtDtFtBtN1L1Czu1StN1L1G1B1V1N2Y1L1Qzu2StDyEtAyEzzyBtByDtGtDzzyB0BtGtByC0ByBtGtCyD0CyCtGtA0BtC0CyCtDtA0D0Dzyzz0E2QtN1M1F1B2Z1V1N2Y1L1Qzu2SzzyC0F0D0E0B0BzztG0AyB0ByDtGyEtAyCzztG0AtAtDtBtG0EtA0FyE0C0E0CyB0DyC0FyE2QtN0A0LzuyEtN1B2Z1V1T1S1NzuyBzyzy%26crD1944451234%26aDwncy_ir_15_25%26osDWindows 7 Ultimate&p={searchTerms}, [85a4ead20684f4422e993a52bb4ae818], %5
PUP.Optional.WinYahoo.A, HKLMSOFTWAREMICROSOFTINTERNET EXPLORERSEARCHSCOPES{0633EE93-D776-472f-A0FF-E1416B8B2E3A} TopResultURLFallback, http://in.yhs4.search.yahoo.com/yhs/search?hspart=iry&hsimp=yhs-fullyhosted_003&type=wncy_ir_15_25¶m1=1¶m2=fD4%26bDIE%26ccDin%26paDWincy%26cdD2XzuyEtN2Y1L1QzutDtDtAtDyCyByD0Ezz0DtDyByC0Bzy0AtN0D0Tzu0StCtByCtBtN1L2XzutAtFtCtDtFtCtDtFtBtN1L1Czu1StN1L1G1B1V1N2Y1L1Qzu2StDyEtAyEzzyBtByDtGtDzzyB0BtGtByC0ByBtGtCyD0CyCtGtA0BtC0CyCtDtA0D0Dzyzz0E2QtN1M1F1B2Z1V1N2Y1L1Qzu2SzzyC0F0D0E0B0BzztG0AyB0ByDtGyEtAyCzztG0AtAtDtBtG0EtA0FyE0C0E0CyB0DyC0FyE2QtN0A0LzuyEtN1B2Z1V1T1S1NzuyBzyzy%26crD1944451234%26aDwncy_ir_15_25%26osDWindows 7 Ultimate&p={searchTerms}, [2dfc526ae3a7b77f15b29bf15fa6a858], %5
PUP.Optional.WinYahoo.A, HKUS-1-5-21-2887370976-2933954842-197170916-1001SOFTWAREMICROSOFTINTERNET EXPLORERSEARCHSCOPES{0633EE93-D776-472f-A0FF-E1416B8B2E3A} URL, http://in.yhs4.search.yahoo.com/yhs/search?hspart=iry&hsimp=yhs-fullyhosted_003&type=wncy_ir_15_25¶m1=1¶m2=fD4%26bDIE%26ccDin%26paDWincy%26cdD2XzuyEtN2Y1L1QzutDtDtAtDyCyByD0Ezz0DtDyByC0Bzy0AtN0D0Tzu0StCtByCtBtN1L2XzutAtFtCtDtFtCtDtFtBtN1L1Czu1StN1L1G1B1V1N2Y1L1Qzu2StDyEtAyEzzyBtByDtGtDzzyB0BtGtByC0ByBtGtCyD0CyCtGtA0BtC0CyCtDtA0D0Dzyzz0E2QtN1M1F1B2Z1V1N2Y1L1Qzu2SzzyC0F0D0E0B0BzztG0AyB0ByDtGyEtAyCzztG0AtAtDtBtG0EtA0FyE0C0E0CyB0DyC0FyE2QtN0A0LzuyEtN1B2Z1V1T1S1NzuyBzyzy%26crD1944451234%26aDwncy_ir_15_25%26osDWindows 7 Ultimate&p={searchTerms}, [a88118a494f666d09234f19b9b6ab34d], %5
PUP.Optional.WinYahoo.A, HKUS-1-5-21-2887370976-2933954842-197170916-1001SOFTWAREMICROSOFTINTERNET EXPLORERSEARCHSCOPES{0633EE93-D776-472f-A0FF-E1416B8B2E3A} TopResultURLFallback, http://in.yhs4.search.yahoo.com/yhs/search?hspart=iry&hsimp=yhs-fullyhosted_003&type=wncy_ir_15_25¶m1=1¶m2=fD4%26bDIE%26ccDin%26paDWincy%26cdD2XzuyEtN2Y1L1QzutDtDtAtDyCyByD0Ezz0DtDyByC0Bzy0AtN0D0Tzu0StCtByCtBtN1L2XzutAtFtCtDtFtCtDtFtBtN1L1Czu1StN1L1G1B1V1N2Y1L1Qzu2StDyEtAyEzzyBtByDtGtDzzyB0BtGtByC0ByBtGtCyD0CyCtGtA0BtC0CyCtDtA0D0Dzyzz0E2QtN1M1F1B2Z1V1N2Y1L1Qzu2SzzyC0F0D0E0B0BzztG0AyB0ByDtGyEtAyCzztG0AtAtDtBtG0EtA0FyE0C0E0CyB0DyC0FyE2QtN0A0LzuyEtN1B2Z1V1T1S1NzuyBzyzy%26crD1944451234%26aDwncy_ir_15_25%26osDWindows 7 Ultimate&p={searchTerms}, [36f34d6fb9d167cf19ad810bb84d827e], %5
Registry Data: 1
PUP.Optional.WinYahoo.A, HKUS-1-5-21-2887370976-2933954842-197170916-1001SOFTWAREMICROSOFTINTERNET EXPLORERMAIN Start Page, http://in.yhs4.search.yahoo.com/yhs/web?hspart=iry&hsimp=yhs-fullyhosted_003&type=wncy_ir_15_25¶m1=1¶m2=fGood: (www.google.com)D1%26bGood: (www.google.com)DIE%26ccGood: (www.google.com)Din%26paGood: (www.google.com)DWincy%26cdGood: (www.google.com)D2XzuyEtN2Y1L1QzutDtDtAtDyCyByD0Ezz0DtDyByC0Bzy0AtN0D0Tzu0StCtByCtBtN1L2XzutAtFtCtDtFtCtDtFtBtN1L1Czu1StN1L1G1B1V1N2Y1L1Qzu2StDyEtAyEzzyBtByDtGtDzzyB0BtGtByC0ByBtGtCyD0CyCtGtA0BtC0CyCtDtA0D0Dzyzz0E2QtN1M1F1B2Z1V1N2Y1L1Qzu2SzzyC0F0D0E0B0BzztG0AyB0ByDtGyEtAyCzztG0AtAtDtBtG0EtA0FyE0C0E0CyB0DyC0FyE2QtN0A0LzuyEtN1B2Z1V1T1S1NzuyBzyzy%26crGood: (www.google.com)D1944451234%26aGood: (www.google.com)Dwncy_ir_15_25%26osGood: (www.google.com)DWindows 7 Ultimate, Bad: (http://in.yhs4.search.yahoo.com/yhs/web?hspart=iry&hsimp=yhs-fullyhosted_003&type=wncy_ir_15_25¶m1=1¶m2=f%3D1%26b%3DIE%26cc%3Din%26pa%3DWincy%26cd%3D2XzuyEtN2Y1L1QzutDtDtAtDyCyByD0Ezz0DtDyByC0Bzy0AtN0D0Tzu0StCtByCtBtN1L2XzutAtFtCtDtFtCtDtFtBtN1L1Czu1StN1L1G1B1V1N2Y1L1Qzu2StDyEtAyEzzyBtByDtGtDzzyB0BtGtByC0ByBtGtCyD0CyCtGtA0BtC0CyCtDtA0D0Dzyzz0E2QtN1M1F1B2Z1V1N2Y1L1Qzu2SzzyC0F0D0E0B0BzztG0AyB0ByDtGyEtAyCzztG0AtAtDtBtG0EtA0FyE0C0E0CyB0DyC0FyE2QtN0A0LzuyEtN1B2Z1V1T1S1NzuyBzyzy%26cr%3D1944451234%26a%3Dwncy_ir_15_25%26os%3DWindows 7 Ultimate),[e544ead2dcae81b5c26a53f5b2549769], %5
Folders: 2
PUP.Optional.OpenCandy, C:UserspanduAppDataRoamingOpenCandy, , [aa7ffac281095cda6f7801bd57acd32d],
PUP.Optional.OpenCandy, C:UserspanduAppDataRoamingOpenCandyB17E680215DD4D76A23AB8D12C5767F4, , [aa7ffac281095cda6f7801bd57acd32d],
Files: 2
PUP.Optional.RazorWeb.A, C:UserspanduAppDataRoamingOpenCandyB17E680215DD4D76A23AB8D12C5767F4setup.exe, , [cc5dfdbfc9c11d1949a53b47fa0ccb35],
PUP.Optional.OpenCandy, C:UserspanduAppDataRoamingPowerISOUpgradePowerISO6.exe, , [55d4863692f8a2940a24fe6fde2814ec],
Physical Sectors: 0
(No malicious items detected)
(end)
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.

See if the following helps: http://en.kioskea.net/faq/8734-files-on-flash-drive-changed-to-shortcuts
-steve
^_^Windows Insider MVP (Security), Moderator Microsoft Community
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
hey
When i was tring to run 'attrib -h -r -s /s /d g:*.*'
acess denied is showingg
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
From the first link I posted, where the attrib command is shown:
Click on Start > Run, type cmd and click OK
Instead, try:
Click on Start, in the search box type cmd, right click on cmd.exe in the results list and select Run as Administrator
-steve
^_^Windows Insider MVP (Security), Moderator Microsoft Community
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
that is also not working
Have u run few antivirus scans accompanied by malwarebyte? Where are you trying to run attrib command ? I mean which location you are trying to execute it?
H.A.V. AravindaDid this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
in all drives
i mean I am trying it for every partition
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
in all drives
i mean I am trying it for every partition
You are supposed to be using the attrib command with the 'G:' replaced by the drive letter for your plugged in flash drive.
-steve
^_^Windows Insider MVP (Security), Moderator Microsoft Community
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
As you mentioned if you have scanned you PC with AVG 2015 and Malwarebyte they are power enough to remove the viruses.
But no one above are capable of re fixing changes done by the virus to your pen drive.
To remove the shortcuts and get your data from the pen drive you should run the CMD command properly.
attrib -s -r -h /s /d *.* K:
K is the drive letter of my pen drive and change it to yours one
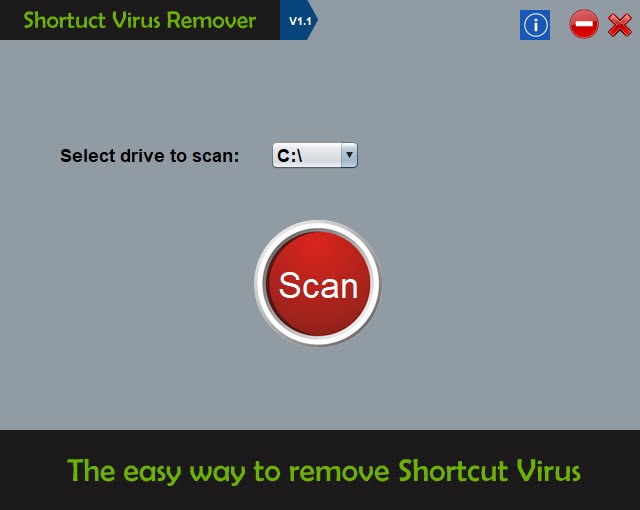
If you are not comfortable with typing commands in CMD use Shortcut Virus Remover.
A simple free application which done the same (attrib -s -r -h /s /d *.*) but very easy to use and very fast.
Download it from www.shortcutvirusremover.com. Your issue will solve.
Virus Shortcut Remover Windows 7 Windows 10
=> Moderator note: The file offered by this poster is not verified as solution for the issue invovlved. Use at your own risk. Please report any problems encountered to this thread.
Did this solve your problem?
Sorry this didn't help.
How To Remove Shortcut Virus From Laptop
Great! Thanks for marking this as the answer.
Shortcut Virus Remover Windows 7 32 Bit
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
Comments are closed.